Web Application Penetration Test for a Fintech Platform
Manual-first penetration testing for a fintech landing page — validating real-world exploitability and strengthening security posture.Client & Project Overview
A European fintech company engaged SiriusOne to conduct a full external penetration test of its marketing website. Although the scope was intentionally narrow, the landing page represented an exposed entry point — requiring rigorous OWASP-aligned validation. The goal was to uncover vulnerabilities, configuration weaknesses, CMS risks, and plugin-level exposure, ensuring the website met modern security standards and that all fixes were verified in a post-remediation retest.
Business Problem
Fintech companies face a threat landscape where even “simple” web surfaces can be exploited for credential harvesting, redirection attacks, SEO poisoning, or supply-chain compromise. Automated scanners previously used by the client detected only superficial issues. They required a manual, structured OWASP Top 10:2025 assessment capable of identifying:
- WordPress misconfigurations
- Plugin & theme vulnerabilities
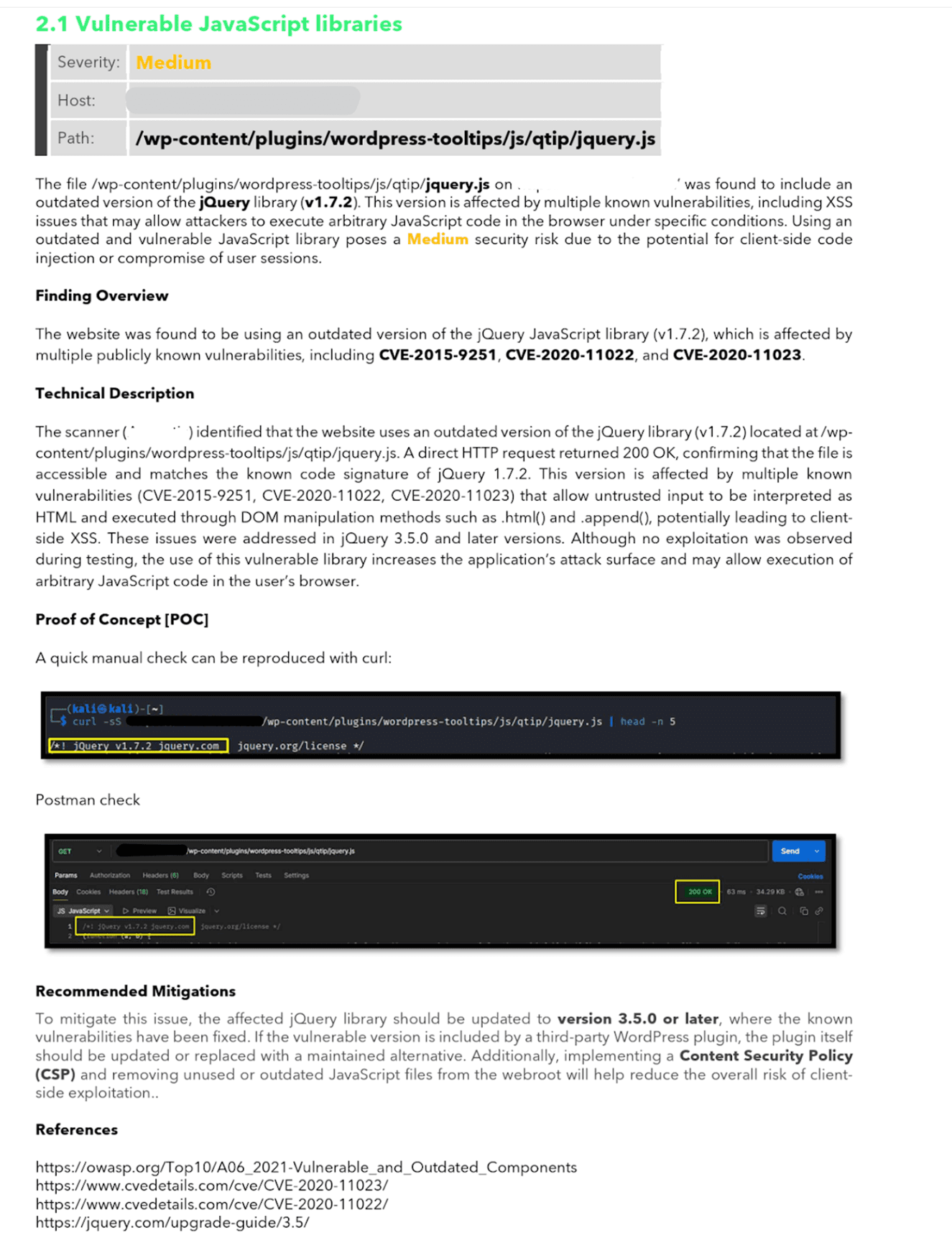
- Endpoint/API exposure
- Input validation flaws
- Authentication weaknesses
- Cloud/infrastructure risks
"Our goal was to bring clarity, predictability, and precision into the validation process. Even a simple landing page can introduce real risk — our job is to ensure it never becomes one."
Eugene Kulchitski
CEO, SiriusOne
Tech Stack
Cloud: Apache / Nginx hosting environment
Platform: WordPress CMS (themes, plugins, REST API)
Security Tools: Burp Suite, OWASP ZAP, Intruder, Nikto, WPScan, Nmap
Dependency & SCA: WordPress scanners, plugin/theme fingerprinting scripts
Frameworks: OWASP Top 10:2025, PTES, SANS Top 25, CVSS v4
#Cybersecurity
#Penetration Testing
#Fintech
Project Timeline

We followed a fast, structured roadmap — ensuring transparent, complete, and repeatable penetration testing.
Duration
1–2 weeks
Effort
25 hours + 5-hour retest bank
Discovery & Research
Day 1
External footprinting, CMS fingerprinting, plugin/theme enumeration, server configuration review.
Design & Prototyping
Day 2
Threat modeling, OWASP Top 10 mapping, WordPress-specific test design, WAF bypass plan.
Development
Days 3–4
Manual exploitation of injection vectors, auth testing, REST API validation, WPScan CVE checks, TLS/header review.
Testing & Security Audit
Day 5
Risk validation, dependency checks, misconfiguration verification, CVSS v4 scoring, evidence collection.
Deployment & Training
+2-week retest window
Delivery of technical report, business impact mapping, remediation workshop, and verification of fixes.
Team involved
Penetration Tester
Manual exploitation, OWASP/PTES aligned testing.
Cybersecurity Analyst
WordPress CMS audit, CVSS scoring, evidence preparation.
Delivery Lead
Scope management, communication, report delivery.
Solution Overview
SiriusOne executed a targeted, manual-first penetration test to harden a WordPress-based landing page — combining CMS-specific analysis, infrastructure review, and full validation of server and application components.
External Web & API Testing
OWASP Top 10 manual testing, input validation flaws, auth bypass attempts, session management review.
WordPress Vulnerability Review
Plugin/theme enumeration, known CVEs, XML-RPC checks, file-upload risks, REST API exposure.
Infrastructure & Configuration Audit
Server header analysis, TLS validation, DNS review, caching/redirect evaluation, hosting misconfiguration checks.
WAF Evasion Validation
Bypass attempts, false-negative testing, rule-set robustness evaluation.
Unified Reporting & Verified Retest
CVSS scoring, PoC evidence, prioritized remediation plan, retest confirmation of resolved issues.
Results
Full Visibility Across the Attack Surface
Critical and high-severity vulnerabilities discovered and documented.
WordPress Deployment Fully Hardened
Configuration fixes applied, insecure components removed, unnecessary endpoints disabled.
Security Strengthened Prior to Exploitation
TLS, header security, and CMS configuration improvements.
100% of Critical Vulnerabilities Resolved
All major issues were validated as fixed during the retest.
Similar
implemented cases: